CDA members who voted for a new party leader will have to vote again after TPM PhD student Jordy San José Sanchez exposed a leak in the political party’s voting webpage.
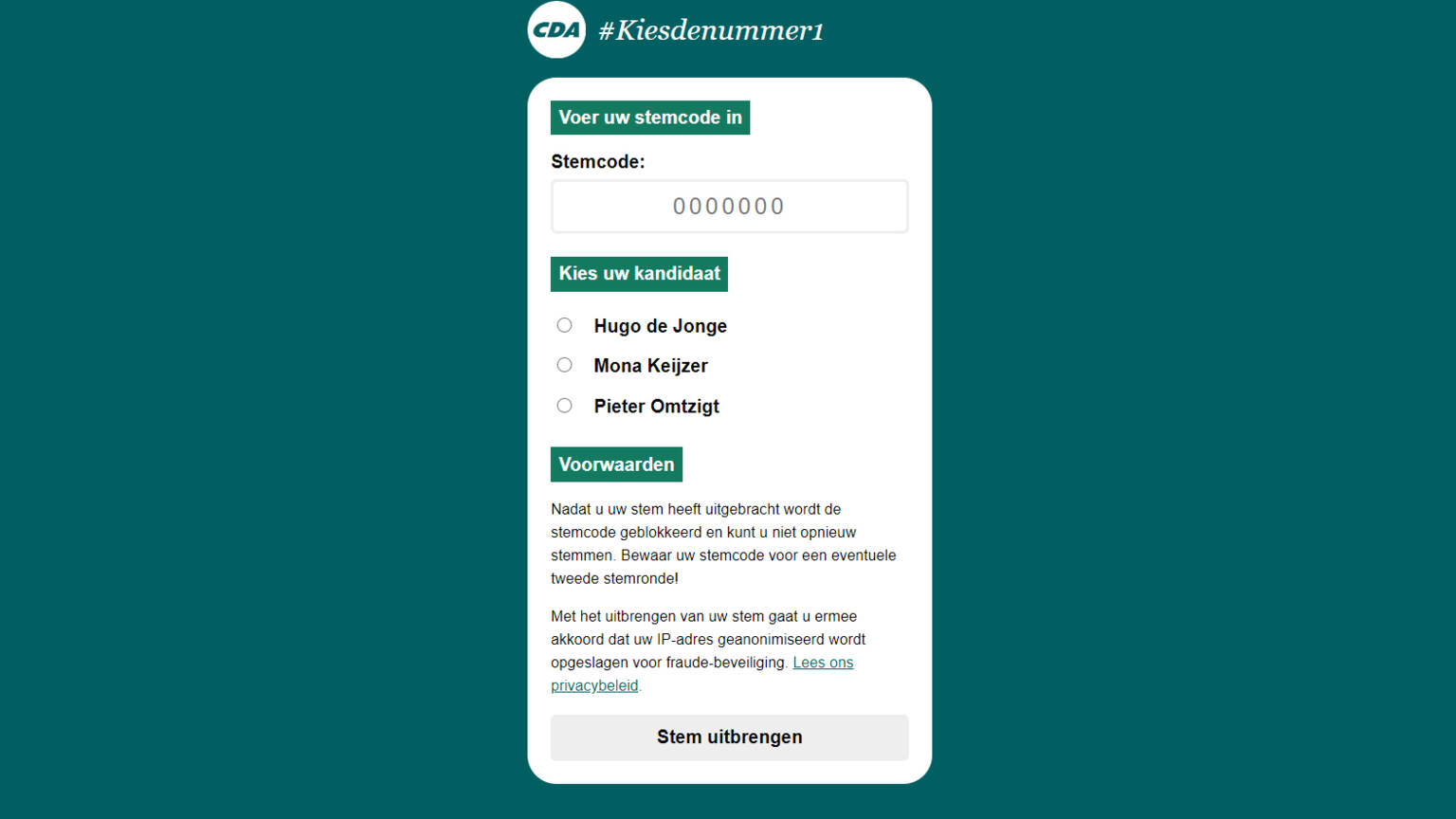
The original voting page on the CDA website. (Picture: CDA)
“It was actually quite simple,” says PhD student Jordy San José Sanchez (Faculty of Technology, Policy and Management) about his discovery. The website of the Christian Democratic Party (CDA) to vote for the party leader is open to the public. Visitors just needed to enter a seven digit numerical code (it said ‘0000000’), after which they could vote for Hugo de Jonge, Mona Keijzer or Pieter Omtzigt as party leader.
San José Sanchez wrote a small programme that generated seven digit codes and released it on the voting page. After he found a matching code three times, and could vote thrice, the PhD student contacted his professor, Prof. Michel van Eeten (Cyber Security). He also informed the CDA of the leak.
Again
The party then decided to re-run the election because it could not guarantee that the election had been fair. “We want to be sure that the election was fair, and we cannot guarantee that now,” said party Chairman Rutger Ploum to the NOS. CDA members will, again, be able to cast their votes from Thursday to Saturday morning.
Postal code
What’s different now? Former naval officer and econometrician San José Sanchez sees some differences. The seven zeros have disappeared from the code window. Voters now also have to enter their member number and their postal code. Huh? Voting is anonymous, isn’t it? The postal code is checked afterwards by a notary, reports the website, ‘so the anonymity of the voter is again guaranteed’. A Captcha has also been added to the page which makes it more difficult to fill in the form automatically because objects from a series of photos need to be recognised. The NOS reports that the CDA has hired the security company Fox-IT.
String
San José Sanchez finds it strange that the CDA is still using the same seven digit voting codes, because it cannot be excluded that someone traced the codes on the previous website. Does he have a better idea? Sending an individual long random string of 20 digits and numbers to each member by email and have them enter it as password, the PhD candidate suggests .

Jordy San José Sanchez investigates the use of artificial intelligence to detect cyber attacks. (Photo: private collection)
Do you have a question or comment about this article?
s.m.bonger@tudelft.nl

Comments are closed.